Everything you need to know about the Petya, er, NotPetya nasty trashing PCs worldwide
This isn't ransomware – it's merry chaos
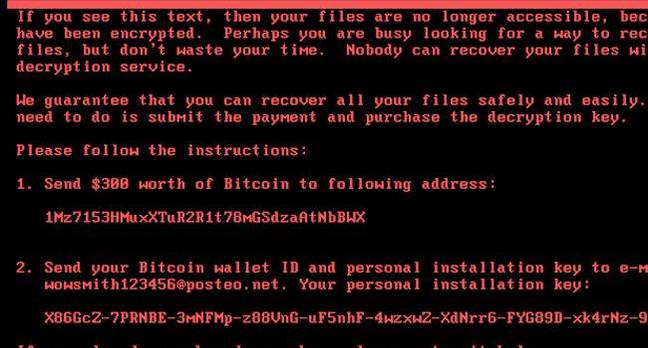
Analysis It is now increasingly clear that the global outbreak of a file-scrambling software nasty targeting Microsoft Windows PCs was designed not to line the pockets of criminals, but spread merry mayhem.
The malware, dubbed NotPetya because it masquerades as the Petya ransomware, exploded across the world on Tuesday, taking out businesses from shipping ports and supermarkets to ad agencies and law firms. Once inside a corporate network, this well-oiled destructive program worms its way from computer to computer, trashing the infected machines' filesystems.
Although it demands about $300 in Bitcoin to unscramble the hostage data, the mechanisms put in place to collect this money from victims in exchange for decryption keys quickly disintegrated. Despite the slick programming behind the fast-spreading malware, little effort or thought was put into pocketing the loot, it appears.
"The superficial resemblance to Petya is only skin deep," noted computer security veteran The Grugq. "Although there is significant code sharing, the real Petya was a criminal enterprise for making money. This [latest malware] is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of ransomware.”
To put it plainly, this code was built to destroy, not extort.
Here's a summary of the NotPetya outbreak:
In Ukraine itself, which appears to be ground zero for the attack, the situation was critical. Large numbers of businesses were caught by the software nasty – the contagion has broken the automatic radiation monitoring systems in Chernobyl, meaning some unlucky scientists are going to have to take readings manually for the time being. Energy companies were hit as well as government agencies.
According to Ukraine's cyber-cops, as well as phishing emails booby-trapped with malware-laden attachments, financial software firm MeDoc was used to infect computers in the ex-Soviet nation. We're told miscreants managed to compromise a software update for the biz's products, which are widely used in the country, so that when it was downloadable and installed by victims it contaminated their network with NotPetya. If this software was running with domain admin access, it would be immediately game over.
MeDoc issued an early statement confessing "our server made a virus attack," but has since U-turned on Facebook, denying that it is responsible.
The tax software maker admitted it was hacked but said its last software update was sent out on June 22, just before Tuesday's attack. However, police said that on June 27 the update servers – upd.me-doc.com.ua – pushed out a 333KB download to customers that unpacked a RUNDLL32.EXE containing the NotPeyta nasty. Oops.
The executable, by the way, lightly XOR encrypts itself and uses faked Microsoft digital signatures in an attempt to fool antivirus scanners. When the nasty started spreading, just two AV engines on the VirusTotal roster detected it as dangerous.
One thing is certain – if you are infected with the malware and it has taken a mixing spoon to your bytes, you're screwed. There doesn't appear to be a way to restore PCs with scrambled filesystems, and no way to pay the ransom, because the Posteo webmail address given to pay the $300 ransom has been shut down.
"Since midday it is no longer possible for the blackmailers to access the email account or send emails," Posteo said. "Sending emails to the account is no longer possible either."
Putin and his pals in action?
The first clue is in the types of files this piece of ransomware encrypts. Typically this kind of malware encrypts everything to make the victim more likely to cough up the digital cash, but in total this ransomware encrypts 65 types of files, from .7z archives and .c source files to .aspx code to .pdf and .php files to PowerPoint and Python to VMware images and Excel spreadsheets.
That might sound like a lot, but the original Petya ransomware that popped up last year encrypted hundreds of file types, and the new code makes some interesting choices in what it encrypts.
"It's very odd," Justin Cappos, assistant professor of security, operating systems and networks at the New York University Tandon School of Engineering told The Register.
"The image types like .png don't seem to be among those encrypted and usually those would be the kinds of things people want to encrypt because the victims will care about their baby pictures, if you were targeting consumers. I find this suspicious; it's targeting code and even Python scripts and Visual Basic to lock down developers' work."
There's also the method of extracting money from the attack. Ransomware has been exploding of late because it makes it easy for criminals to collect funds without having to recruit a lot of money mules around the world to harvest payments.
Bitcoin has helped with this and, as you'd expect, this infection also asks for the digital currency but with a crucial difference. This time, users wanting to get their files back had to email details to a specific address.
This is neither normal or sensible, since the malware writers must have known that the email address would be shut down quickly, which cut off access to funds. This is not how criminals looking to make a quick buck operate.
Another hint comes in the timing of the attack. Tomorrow, June 28, is a national holiday in Ukraine, its annual Constitution Day. Criminal hackers typically attack on holidays and weekends to avoid detection, but doing so the day before looks like an attempt to cause maximum disruption for the largest number of people in the country.
Who is Ukraine's main enemy at the moment? Russia, since it's currently fighting a proxy in the country by supporting the Donetsk People's Republic that has set itself up in the east of the country. Russia has also been accused of hacking Ukrainian systems in the past.
That said, Russian firms have been hit by the ransomware too. State oil giant Rosneft has reported infections, although it says oil productions and processing wasn't harmed in the outbreak, and local steel maker Evraz has also been infected.
As is so often the case in online attacks, we may never know the truth behind the source of the infection, but Interpol and police forces in at least three countries are investigating the source and motivations behind the attacks. Microsoft will be doing its own detective work and says Defender has been updated to block the ransomware.
"Our initial analysis found that the ransomware may use multiple techniques to spread, including one which was addressed by a security update previously provided for all platforms from Windows XP to Windows 10," a spokesperson told The Reg.
"As ransomware also typically spreads via email, customers should exercise caution when opening unknown files. We are continuing to investigate and will take appropriate action to protect customers."
In the meantime, the best advice for dealing with ransomware hasn't changed since yesterday. Ensure that you take regular and complete backups, patch software as soon as possible, and disable any unwanted features or open ports that can be closed off. ®
The malware, dubbed NotPetya because it masquerades as the Petya ransomware, exploded across the world on Tuesday, taking out businesses from shipping ports and supermarkets to ad agencies and law firms. Once inside a corporate network, this well-oiled destructive program worms its way from computer to computer, trashing the infected machines' filesystems.
Although it demands about $300 in Bitcoin to unscramble the hostage data, the mechanisms put in place to collect this money from victims in exchange for decryption keys quickly disintegrated. Despite the slick programming behind the fast-spreading malware, little effort or thought was put into pocketing the loot, it appears.
"The superficial resemblance to Petya is only skin deep," noted computer security veteran The Grugq. "Although there is significant code sharing, the real Petya was a criminal enterprise for making money. This [latest malware] is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of ransomware.”
To put it plainly, this code was built to destroy, not extort.
Here's a summary of the NotPetya outbreak:
- The malware uses a bunch of tools to move through a network, infecting machines as it goes. It uses a tweaked build of open-source Minikatz to extract network administrator credentials out of the machine's running memory. It uses these details to connect to and execute commands on other machines using PsExec and WMIC to infect them. It can either scan subnets for devices or, if it's running on a domain controller, use the DHCP service to identify known hosts.
- It also uses a modified version of the NSA's stolen and leaked EternalBlue SMB exploit, previously used by WannaCry, plus the agency's stolen and leaked EternalRomance SMB exploit, to infect other systems by injecting malicious code into them. These cyber-weapons attack vulnerabilities were patched by Microsoft earlier this year, so the credential theft is usually more successful, at least at places that are on top of their Windows updates.
- Crucially, NotPetya seeks to gain administrator access on a machine and then leverages that power to commandeer other computers on the network: it takes advantage of the fact that far too many organizations employ flat networks in which an administrator on one endpoint can control other machines, or sniff domain admin credentials present in memory, until total control over the Windows network is achieved.
- One way to gain admin access is to use the NSA exploits. Another way is to trick a user logged in as an admin or domain admin into running a booby-trapped email attachment that installs and runs the malware with high privileges. Another way is to feed a malicious software update to an application suite running as admin or domain admin, which starts running the malware on the corporate network again with high privileges. It is understood NotPetya got into corporate networks as an admin via a hijacked software update for a Ukrainian tax software tool, and via phishing emails.
- With admin access, the software nasty can not only lift credentials out of the RAM to access other internal systems, it can rewrite the local workstation's hard drive's MBR so that only the malware starts up when the machine reboots, rather than Windows, allowing it to display the ransom note and demand an unlock key; it can also encrypt the NTFS filesystem tables and files on the drive. NotPetya uses AES-128 to scramble people's data.
- Needless to say, don't pay the ransom – there's no way to get the necessary keys to restore your documents. It appears the malware doesn't provide enough information to the extortionists for them to generate a correct unlock key, so it would be impossible to obtain a working decryption key from the crims. And the means to contact the miscreants after paying the money is now shut off, so you're out of luck regardless.
- Not only should you patch your computers to stop the SMB exploits, disable SMBv1 for good measure, and block outside access to ports 137, 138, 139 and 445, you must follow best practices and not allow local administrators carte blanche over the network – and tightly limit access to domain admins. You'd be surprised how many outfits are too loose with their admin controls.
- The precise affected versions of Windows aren't yet known, but we're told Windows 10's Credentials Guard thwarts NotPetya's password extraction from memory.
- Creating the read-only file C:\Windows\perfc.dat on your computer prevents the file-scrambling part of NotPetya running, but doesn't stop it spreading on the network. Note, the software is designed to spread internally for less than an hour and then kicks in; it doesn't attempt to spread externally across the internet like WannaCry did.
In the beginning
So far, the vast majority of infections have occurred in Ukraine and Russia, but some big names in the West have also suffered. International advertising conglomerate WPP was taken offline (even its website was down), global law firm DLA Piper was infected and, most worryingly, shipping goliath Maersk is warning of a worldwide outage that could seriously bork the global transport supply chain. Computer terminals in major ports were borked for hours by the malware.In Ukraine itself, which appears to be ground zero for the attack, the situation was critical. Large numbers of businesses were caught by the software nasty – the contagion has broken the automatic radiation monitoring systems in Chernobyl, meaning some unlucky scientists are going to have to take readings manually for the time being. Energy companies were hit as well as government agencies.
According to Ukraine's cyber-cops, as well as phishing emails booby-trapped with malware-laden attachments, financial software firm MeDoc was used to infect computers in the ex-Soviet nation. We're told miscreants managed to compromise a software update for the biz's products, which are widely used in the country, so that when it was downloadable and installed by victims it contaminated their network with NotPetya. If this software was running with domain admin access, it would be immediately game over.
MeDoc issued an early statement confessing "our server made a virus attack," but has since U-turned on Facebook, denying that it is responsible.
The tax software maker admitted it was hacked but said its last software update was sent out on June 22, just before Tuesday's attack. However, police said that on June 27 the update servers – upd.me-doc.com.ua – pushed out a 333KB download to customers that unpacked a RUNDLL32.EXE containing the NotPeyta nasty. Oops.
The executable, by the way, lightly XOR encrypts itself and uses faked Microsoft digital signatures in an attempt to fool antivirus scanners. When the nasty started spreading, just two AV engines on the VirusTotal roster detected it as dangerous.
What's in a name?
While it was first assumed that the malware was a new strain of the Petya ransomware family that surfaced last year, that is now in doubt due to some key differences in code. The changes are so striking that Kaspersky Lab has gone as far as to dub the code "NotPetya."One thing is certain – if you are infected with the malware and it has taken a mixing spoon to your bytes, you're screwed. There doesn't appear to be a way to restore PCs with scrambled filesystems, and no way to pay the ransom, because the Posteo webmail address given to pay the $300 ransom has been shut down.
"Since midday it is no longer possible for the blackmailers to access the email account or send emails," Posteo said. "Sending emails to the account is no longer possible either."
Putin and his pals in action?
The first clue is in the types of files this piece of ransomware encrypts. Typically this kind of malware encrypts everything to make the victim more likely to cough up the digital cash, but in total this ransomware encrypts 65 types of files, from .7z archives and .c source files to .aspx code to .pdf and .php files to PowerPoint and Python to VMware images and Excel spreadsheets.
That might sound like a lot, but the original Petya ransomware that popped up last year encrypted hundreds of file types, and the new code makes some interesting choices in what it encrypts.
"It's very odd," Justin Cappos, assistant professor of security, operating systems and networks at the New York University Tandon School of Engineering told The Register.
"The image types like .png don't seem to be among those encrypted and usually those would be the kinds of things people want to encrypt because the victims will care about their baby pictures, if you were targeting consumers. I find this suspicious; it's targeting code and even Python scripts and Visual Basic to lock down developers' work."
There's also the method of extracting money from the attack. Ransomware has been exploding of late because it makes it easy for criminals to collect funds without having to recruit a lot of money mules around the world to harvest payments.
Bitcoin has helped with this and, as you'd expect, this infection also asks for the digital currency but with a crucial difference. This time, users wanting to get their files back had to email details to a specific address.
This is neither normal or sensible, since the malware writers must have known that the email address would be shut down quickly, which cut off access to funds. This is not how criminals looking to make a quick buck operate.
Another hint comes in the timing of the attack. Tomorrow, June 28, is a national holiday in Ukraine, its annual Constitution Day. Criminal hackers typically attack on holidays and weekends to avoid detection, but doing so the day before looks like an attempt to cause maximum disruption for the largest number of people in the country.
Who is Ukraine's main enemy at the moment? Russia, since it's currently fighting a proxy in the country by supporting the Donetsk People's Republic that has set itself up in the east of the country. Russia has also been accused of hacking Ukrainian systems in the past.
That said, Russian firms have been hit by the ransomware too. State oil giant Rosneft has reported infections, although it says oil productions and processing wasn't harmed in the outbreak, and local steel maker Evraz has also been infected.
As is so often the case in online attacks, we may never know the truth behind the source of the infection, but Interpol and police forces in at least three countries are investigating the source and motivations behind the attacks. Microsoft will be doing its own detective work and says Defender has been updated to block the ransomware.
"Our initial analysis found that the ransomware may use multiple techniques to spread, including one which was addressed by a security update previously provided for all platforms from Windows XP to Windows 10," a spokesperson told The Reg.
"As ransomware also typically spreads via email, customers should exercise caution when opening unknown files. We are continuing to investigate and will take appropriate action to protect customers."
In the meantime, the best advice for dealing with ransomware hasn't changed since yesterday. Ensure that you take regular and complete backups, patch software as soon as possible, and disable any unwanted features or open ports that can be closed off. ®





