Malware Infections of POS Networks Are Multiplying
By Tracy Kitten, May 27, 2014. Follow Tracy @FraudBlogger

The number of point-of-sale networks infected with new and enhanced strains of retail-oriented malware has significantly increased, researchers say. As a result, they predict that retailer breaches that expose everything from card data to personally identifiable information will continue to grow.
In the most recent development, cyberintelligence firm IntelCrawler last week described attacks in nearly 40 nations, including the U.S., using a new type of POS malware known as Nemanja.
It's just one of many emerging malware strains attacking domestic and international payments systems, says Curt Wilson, senior research analyst at online security firm Arbor Networks.
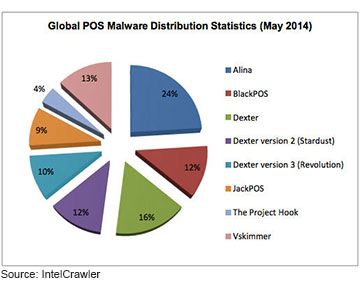
Wilson recently blogged about how POS malware attacks have evolved over the last five years. Today's attacks often begin with "lateral" attacks against third-party vendors to gain credentials that cybercriminals then can use to infiltrate a retailer's POS system, as was the case in the Target Corp. attack, he says.
Major Botnet
Nemanja, which Intelcrawler claims is linked to the compromise of more than 1,000 POS systems globally, is likely the biggest botnet affecting POS terminals, says Andrew Komarov, Intelcrawler's CEO.So far, more than 1,478 hosts in nearly 40 countries have been infected by Nemanja, he says. While actual fraud losses linked to these compromises are not yet known, Komarov believes as many as a half million debit and credit cards could have been exposed.
The documented attacks involving Nemanja have affected mainly small businesses and grocery stores, Komarov says. "[Nemanja] was operated by pretty large gang of cybercriminals who specialized in credit cards fraud," he points out.
"Not only were POS terminals compromised, but also back-office systems of retailers and grocery stores," he says. "The malware has key-logging support and a self-delete option," meaning the hackers have the ability to delete the malware from the system at any time if they suspect their intrusion has been detected, Komarov says.
"The key-logger helps the bad actors gather additional information, which may help them organize a large breach and compromise the network infrastructure," he adds.
In some cases, Nemanja was able to penetrate POS networks through a remote-access portal, using default passwords, IntelCrawler found. In other cases, the malware infiltrated the system using a drive-by-download attack or by breaching the network perimeter. And in a few instances, IntelCrawler believes an insider's network credentials may have been compromised or knowingly shared with cybercriminals.
POS Malware: Then and Now
Nemanja is a prime example of emerging retail malware attacks the security industry has identified in recent months, Wilson says."All indicators that we have at this time suggest that Nemanja is yet another in a long line of memory-scraping POS malware," he says. "Organizations at risk must be well aware of this vulnerability and ensure adequate protection and monitoring of all systems associated with point-of-sale infrastructure."
Today's retail attacks are often fed by the takeover of POS terminals used as command and control centers for future attacks, he says.
And more attacks like this are already under way, Wilson says. "Arbor is aware of other hostile activity directed toward the POS infrastructure, and our awareness of this, plus the volume of POS malware, indicates that this serious problem continues, with attackers most likely emboldened by the success of large-scale compromise and theft of card data."
Al Pascual, a senior fraud analyst specializing in security and fraud for consultancy Javelin Strategy & Research, says Nemanja is similar to other POS malware strains such as Dexter and BlackPOS.
"There has been a surge of malware development in Eastern Europe as cybercrime groups pay for the best talent and newest schemes," he says. "Botnets can't be identified and shut down fast enough, nor can most of those responsible be arrested in meaningful enough numbers to prevent this trend from continuing. ... Retailers around the world need to do more to harden their systems and prevent data exfiltration. Right now, they are the low-hanging fruit."
Dispelling Myths
The global nature of these attacks is dispelling certain myths about card security, says Andreas Baumhof, chief technology officer at malware research firm ThreatMetrix.Chip and PIN card technology, which helps to prevent skimming-related card breaches, is no defense against the emerging POS attacks the payments industry is facing, he says. Even with cards that conform to the Europay, MasterCard, Visa standard, compromises linked to attacks such as Nemanja would not be prevented, he contends.
The payments industry's rally to migrate to EMV chip cards in the U.S., to replace the legacy magnetic-stripe cards still commonly used, isn't likely to have a huge impact on curbing card compromises, adds Arbor's Wilson.
"I've seen experts say that chip and PIN will change the landscape a lot, but these attackers are smart and they have found ways around all types of things," he says. "We still see point-of-sale compromises in Europe, where they have chip and PIN. Even with the chip, there is still opportunity for card data to be stolen there."
The best defense is immediate intrusion detection, which means organizations have to understand what legitimate network traffic looks like so that they can pick up on anomalies sooner, Wilson explains.
Because so many new strains are emerging daily, focusing solely on malware detection is a losing battle, he adds. "But if they focus on activity on the host or on the network, they can question why certain POS commands are showing up. To do this, you have to monitor the internal network."
http://www.databreachtoday.com/more-retailer-breaches-on-way-a-6874/p-2
No comments:
Post a Comment